Release Date: October 8, 2024
SAP Security Note: 3454858
Component: SAP NetWeaver Application Server for ABAP and ABAP Platform
Priority: Medium
Category: Information Disclosure
CVE Identifier: CVE-2024-37180
Overview
A notable security vulnerability, identified as CVE-2024-37180, has been detected in the SAP NetWeaver Application Server for ABAP and ABAP Platform. This vulnerability allows attackers to access remote-enabled function modules without the necessary authorization controls, potentially leading to unauthorized information disclosure. Although the impact on confidentiality is categorized as low, the ability to access function modules that should remain restricted poses a significant security concern that necessitates prompt attention.
Vulnerability Details
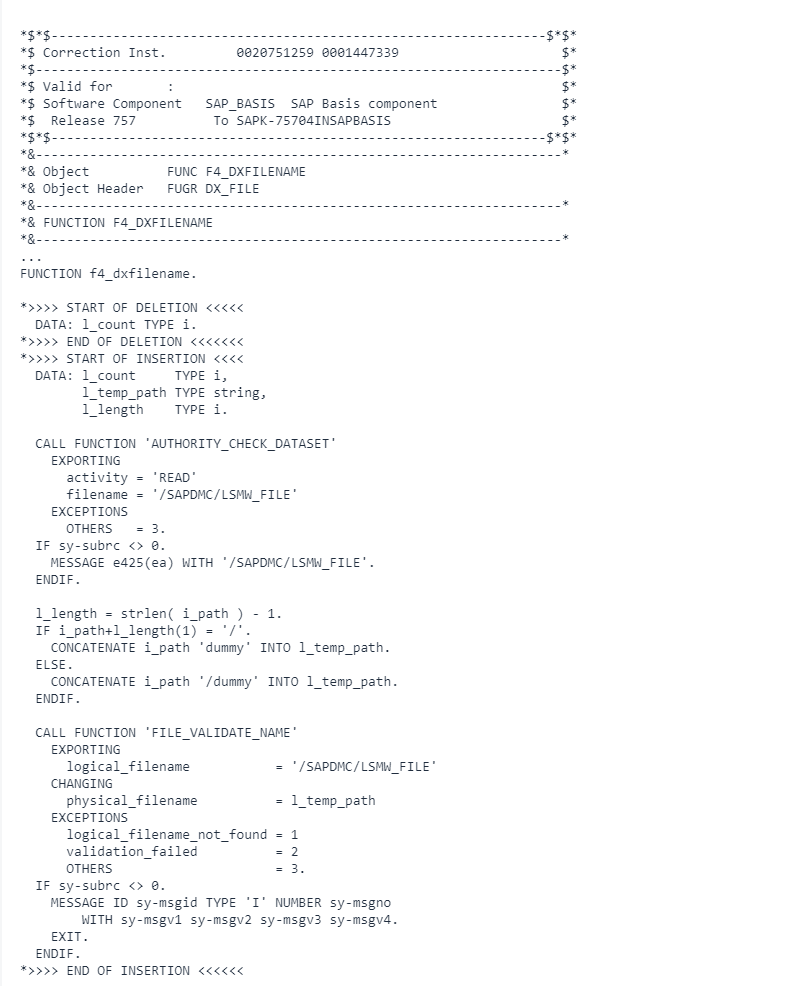
The root cause of CVE-2024-37180 lies in the improper restriction of access to the function module F4_DXFILENAME_TOPRECURSION. This function module inadequately limits access to file system information, enabling attackers to traverse directories beyond intended boundaries. Consequently, unauthorized users can exploit this vulnerability to read non-sensitive information from the application server, undermining the application’s confidentiality measures.
Impact Assessment
This vulnerability affects all installations of SAP NetWeaver Application Server for ABAP and ABAP Platform that utilize the F4_DXFILENAME_TOPRECURSION function module. The primary risk involves unauthorized access to specific file system paths, which could be leveraged to gather information that, while not classified as highly sensitive, still contributes to a broader understanding of the system’s structure and data. Although the immediate impact is limited to information disclosure, it can serve as a stepping stone for more severe attacks if left unaddressed.
Mitigation and Remediation
To mitigate the risks associated with CVE-2024-37180, SAP has released Security Note 3454858, which includes essential support packages and correction instructions. Implementing these updates is crucial to ensuring that access to the F4_DXFILENAME_TOPRECURSION function module is appropriately restricted. The updated security note introduces validation mechanisms that confine user access to the predefined logical file name /SAPDMC/LSMW_FILE through the FILE transaction. This restriction effectively prevents users from navigating to unauthorized directories.
Administrators should follow the detailed instructions provided in the security note to apply the necessary patches. It is also advisable to review and, if necessary, update the logical file path definitions to include any additional directories that users may require access to, ensuring they are properly maintained within the FILE transaction. Additionally, verifying that users have the appropriate read authorizations for the logical file name SAPDMC/LSMW_FILE will further enhance the security posture of the system.