⚠️ CHECK IF YOU’RE VULNERABLE OR COMPROMISED
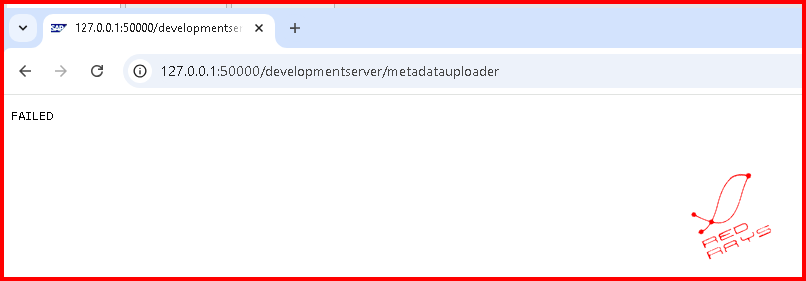
Vulnerable URL Path: /developmentserver/metadatauploader
How to Check If You’re Vulnerable:
- Test if the following URL is accessible without authentication:
https://[your-sap-server]/developmentserver/metadatauploader - If you can access this page without being prompted for credentials, your system is vulnerable.
Signs of Exploitation in Logs:
- Look for unauthorized access attempts to the
/developmentserver/metadatauploaderpath - Check for unexpected file uploads in web server logs
- Search for unusual execution patterns or suspicious processes on your SAP server
- Monitor for unauthorized outbound connections from your SAP systems
If you detect any of these indicators, assume your system may be compromised and initiate your incident response procedures immediately.
PoC
Overview
SAP has recently released a critical security patch for a severe vulnerability in SAP NetWeaver Visual Composer that has been actively exploited in the wild. The vulnerability, tracked as CVE-2025-31324, was patched just hours ago with the release of SAP Security Note 3594142.
This high-severity vulnerability received a CVSS score of 10.0 (Critical), indicating the maximum possible risk level. The flaw allows unauthenticated remote attackers to execute malicious code on vulnerable systems through a file upload mechanism, potentially leading to complete system compromise.
Vulnerability Details
The vulnerability exists specifically in the Metadata Uploader component of SAP NetWeaver Visual Composer. According to SAP’s security advisory:
- Vulnerability Type: Missing Authorization Check (CWE-434 – Unrestricted Upload of File with Dangerous Type)
- Affected Component: EP-VC-INF (Enterprise Portal > Visual Composer > Visual Composer Infrastructure), Version 17
- CVSS Score: 10.0 (Critical)
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Impact: High impact on confidentiality, integrity, and availability
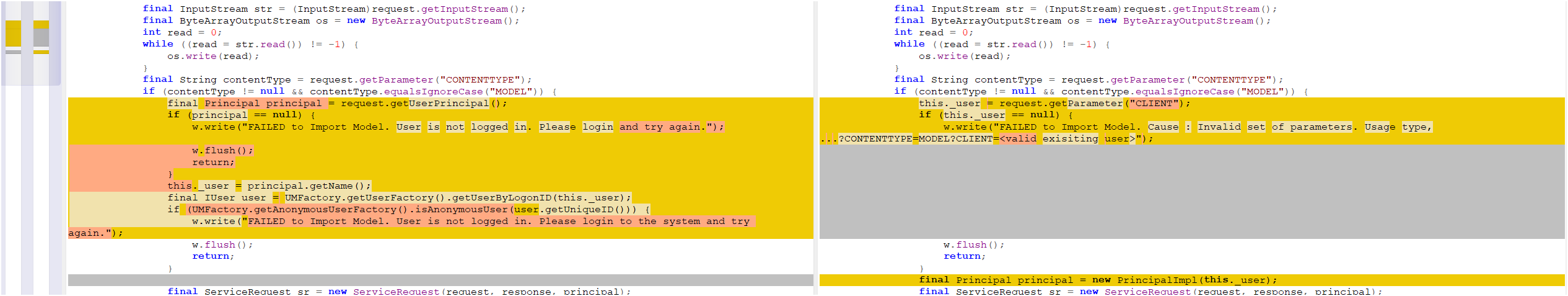
The core issue stems from the absence of proper authorization checks in the Metadata Uploader component, which allows unauthenticated attackers to upload potentially malicious executable binaries to affected systems. If exploited, this vulnerability could lead to a full compromise of affected systems, impacting the confidentiality, integrity, and availability of business-critical data and applications.
Technical Analysis
The vulnerability is particularly dangerous due to several factors:
- No Authentication Required: Attackers don’t need valid credentials to exploit this vulnerability.
- Low Attack Complexity: The attack is relatively straightforward to execute.
- No User Interaction: Exploitation doesn’t require any action from users or administrators.
- High Impact: Successful exploitation potentially gives attackers full control over the affected system.
The flaw exists in the authorization mechanism of the Metadata Uploader, which fails to properly validate that users have the appropriate permissions before allowing file uploads. This oversight allows attackers to bypass security controls and upload malicious binaries that can then be executed on the server.
Real-World Impact
Organizations using vulnerable versions of SAP NetWeaver Visual Composer are at significant risk. The vulnerability could allow attackers to:
- Gain unauthorized access to sensitive business data
- Modify critical business processes
- Disrupt availability of essential SAP services
- Establish persistence within the network
- Pivot to other systems within the infrastructure
Industries relying heavily on SAP solutions, including manufacturing, healthcare, financial services, and critical infrastructure, are particularly at risk from this vulnerability.
Mitigation Steps
SAP has provided a security patch through Security Note 3594142. Organizations are strongly advised to implement the following measures immediately:
- Apply the Latest Patch: Implement SAP Security Note 3594142 as soon as possible.
- Restrict Access: Until patches can be applied, restrict access to the Metadata Uploader component.
- Review External Exposure: Ensure only authenticated users have upload permissions to SAP components.
- Implement Workaround: For organizations unable to patch immediately, SAP has provided a temporary workaround based on the scenario from KBA 3593336.
Patch Details
The security note includes several Support Package patches for VISUAL COMPOSER FRAMEWORK 7.50:
- SP033 (000000)
- SP028 (000001)
- SP029 (000001)
- SP030 (000001)
- SP031 (000001)
- SP027 (000002)
- SP032 (000000)
Detection and Response
Log Analysis for Detecting Exploitation
Check your web server access logs for requests to the vulnerable endpoint:
/developmentserver/metadatauploaderLook for patterns like:
- POST requests to this endpoint, especially from external IP addresses
- Successful requests (HTTP 200 status codes) that weren’t authenticated
- Any file upload activity to this path
Sample Log Patterns to Search For:
"POST /developmentserver/metadatauploader HTTP/1.1" 200
"multipart/form-data" + "/developmentserver/metadatauploader"Conclusion
This critical vulnerability in SAP NetWeaver Visual Composer represents a significant risk to organizations using this component. With active exploitation already observed in the wild, immediate remediation is essential to prevent potential data breaches and system compromises.
RedRays recommends treating this as a highest-priority security update and implementing the provided patches as soon as possible. For organizations unable to patch immediately, implementing the recommended workarounds and enhanced monitoring is crucial to minimize risk exposure.
We will continue to monitor the situation and provide updates as more information becomes available.
For more information and technical assistance, contact the RedRays Security Team at [email protected]