Services
SAP Security Training
SAP Through the Eyes of an Attacker
Online SAP Security Training by RedRays is a comprehensive program designed to empower both seasoned professionals and beginners with in-depth knowledge and hands-on skills to secure critical SAP ERP systems. The course covers the fundamental concepts of the SAP environment, including the architectures of SAP ABAP, SAP NetWeaver, SAP AS Java, and SAP Cloud Connector.
A special emphasis is placed on modern technologies such as SAP Fiori and S/4HANA. Participants will explore SAP Fiori's integration with OData and UI5, which delivers an intuitive, modern user interface that enhances the overall SAP experience. Additionally, the course delves into S/4HANA, the next-generation ERP platform built on the in-memory HANA database, highlighting its role in optimizing business processes and driving digital transformation.
Throughout the training, you will engage in real-world scenarios and hands-on labs covering threat analysis, vulnerability assessment, and attack mitigation techniques. Topics include RFC vulnerabilities, attacks on SAP NW Java, privilege escalation methods, and reverse engineering of SAP patches for both ABAP and JAVA environments. Each day features a 6-hour session followed by an interactive Q&A to ensure comprehensive understanding.
Agenda
Our meticulously structured two-day program balances theoretical knowledge with extensive hands-on exercises. The training is organized as a progressive journey through the SAP security landscape, covering all critical components and attack vectors that security professionals need to understand.
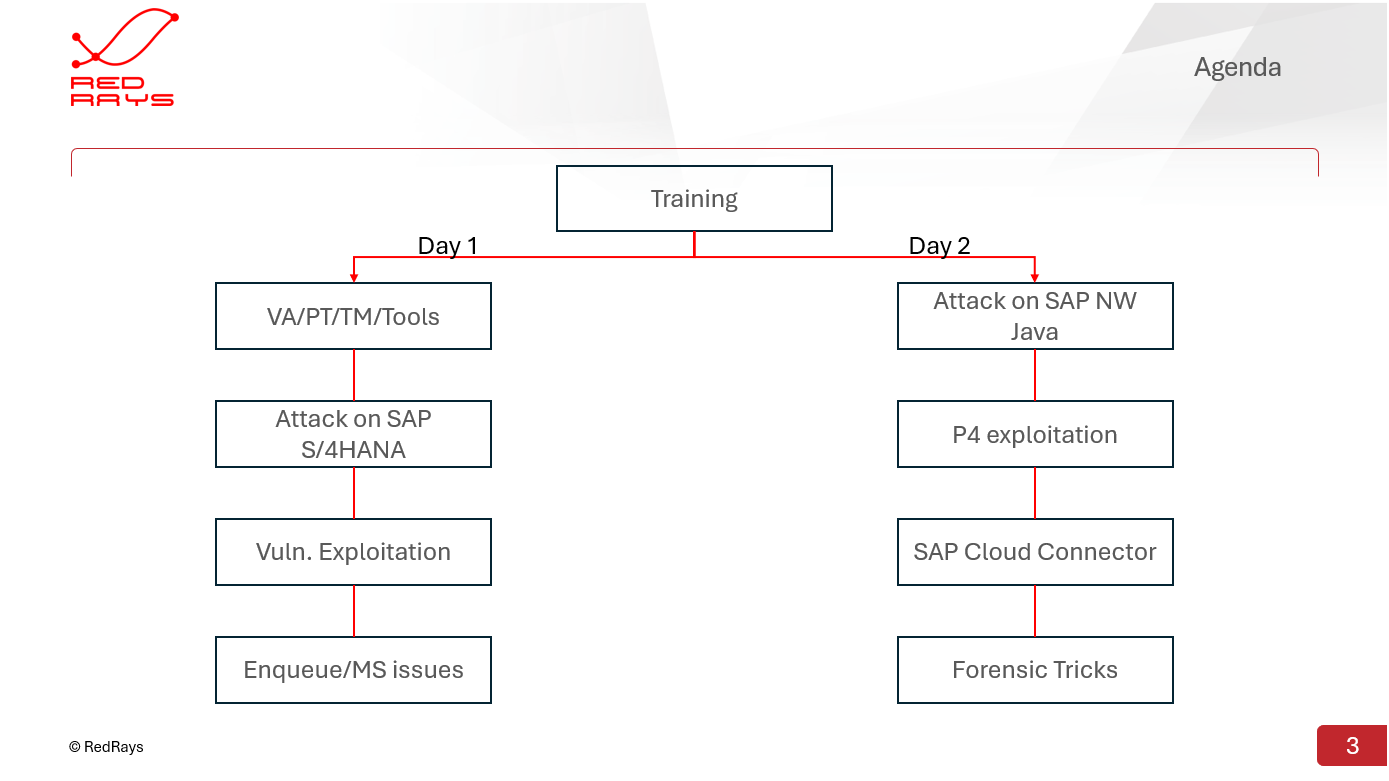
Day 1
VA/PT/TM/Tools
Fundamental methodologies for security assessment, including Vulnerability Assessment, Penetration Testing, and Threat Modeling specifically for SAP environments.
Attack on SAP S/4HANA
Exploring common and advanced vulnerabilities in SAP ECC, S/4HANA, Business Suite, and NetWeaver AS ABAP.
Vuln. Exploitation
Deep dive into vulnerability exploitation techniques specific to SAP systems, including RFC callback attacks and debug mode exploitation.
Enqueue/MS issues
Security issues with SAP Enqueue Server and Message Server components, including "phantom attacker" techniques to bypass SAP ABAP lock functionality.
Day 2
Attack on SAP NW Java
Critical vulnerabilities in the Java stack of SAP NetWeaver, including authentication bypasses, directory traversals, and Java deserialization attacks.
P4 exploitation
Techniques for exploiting vulnerabilities in SAP's proprietary P4 remote method invocation technology.
SAP Cloud Connector
Security issues in SAP Cloud Connector, which is used to securely connect cloud applications with on-premises systems.
Forensic Tricks
Essential forensic techniques for SAP environments, including 5 basic techniques to identify compromises and threats.
Instructor

Led by Vahagn Vardanian – a recognized expert in SAP security with over a decade of experience and a track record of identifying more than 150 vulnerabilities – this course equips you with the practical expertise needed to protect your SAP landscape against sophisticated cyber threats.

