Vulnerability Details
- CVE ID: CVE-2024-42374
- CVSS v3.0 Base Score: 8.2 (High)
- Affected Component: SAP BEx Web Java Runtime Export Web Service
- Vulnerability Type: XML Injection
Description
The vulnerability affects the BEx Web Java Runtime Export Web Service, which fails to sufficiently validate XML documents accepted from untrusted sources. This flaw allows an attacker to potentially retrieve information from the SAP ADS system and exhaust the number of XMLForm services, rendering the SAP ADS PDF creation functionality unavailable.
Impact
If successfully exploited, this vulnerability can lead to:
- Confidentiality breach: Unauthorized retrieval of information from the SAP ADS system
- Availability disruption: Potential denial of service for SAP ADS rendering (PDF creation)
The high CVSS score of 8.2 underscores the severity of this vulnerability and the urgent need for patching.
Affected Versions
- SAP NetWeaver BI 7.50
- Specific to PDF export using Java ALV and ADS
PoC
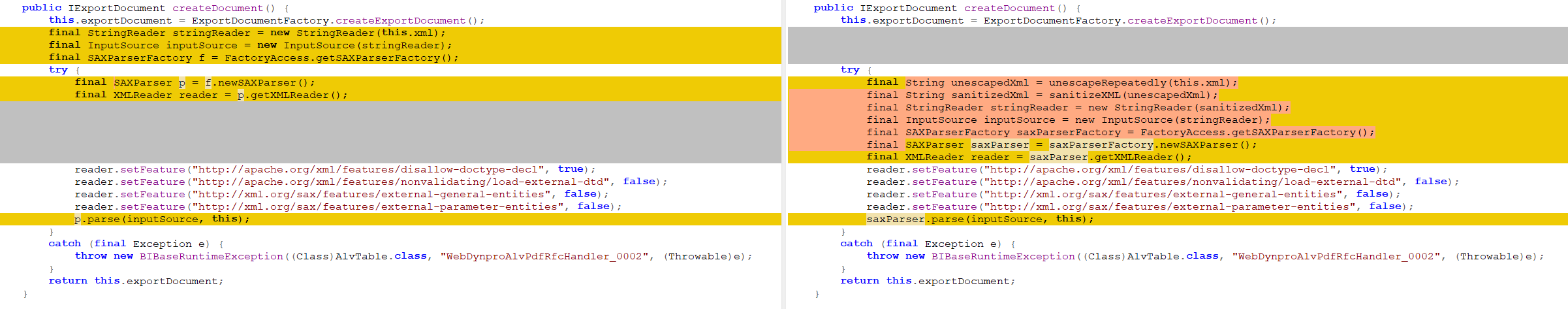
Mitigation
SAP has released patches to address this vulnerability. The XML parser has been updated to check for vulnerabilities in the XML input.
Patch Information
For SAP NetWeaver BI 7.50 systems:
- Import the BI Java Patch for SAP NW 7.50 BI JAVA into your BI-System
- Refer to SAP Note 3377693 for detailed delivery information and other available patch options
- Also consult SAP Note 1512355 for the delivery schedule
Patches are available for the following components:
- BI BASE EXPORT SERVICES 7.50
- BI BASE FOUNDATION 7.50
- BI BASE SERVICES 7.50
It is strongly recommended that all affected organizations apply these patches as soon as possible.
Workaround
SAP has not provided any workaround for this vulnerability. The only mitigation is to apply the provided patches.
Recommendations
- Identify all instances of SAP NetWeaver BI 7.50 in your organization, particularly those using BEx Web Java Runtime Export Web Service.
- Prioritize the application of the security patches based on the criticality of the affected systems.
- Conduct a thorough security assessment of your BI environment to identify any potential compromise.
- Review and enhance your input validation mechanisms, especially for XML documents from untrusted sources.
- Monitor system logs for any suspicious activities, particularly those related to PDF exports and ADS rendering.
Conclusion
The discovery of CVE-2024-42374 highlights the ongoing importance of robust security measures in business intelligence platforms, particularly in data export functionalities. Organizations using SAP NetWeaver BI should treat this vulnerability with high urgency and apply the patches immediately to protect their critical business data and operations.






