Unauthenticated Insecure Deserialization Enabling Complete System Takeover
🚨 MAXIMUM SEVERITY - EMERGENCY RESPONSE REQUIRED
SAP has disclosed a maximum severity CVSS 10.0 vulnerability in SAP NetWeaver Application Server Java. This critical insecure deserialization flaw in the RMI-P4 module allows completely unauthenticated remote attackers to execute arbitrary operating system commands. This represents the highest possible threat level and requires immediate emergency patching across all SAP Java environments.
Vulnerability Overview
CVE-2025-42944 is the most critical SAP vulnerability disclosed in 2025. This insecure deserialization flaw exists in the RMI-P4 (Remote Method Invocation - Proprietary Protocol 4) module of SAP NetWeaver Application Server Java, a foundational component deployed across thousands of enterprise SAP installations worldwide.
The vulnerability achieves the maximum possible CVSS score of 10.0 because it combines every worst-case characteristic: no authentication required, low attack complexity, no user interaction needed, network exploitation, and complete system compromise with changed scope. Remote attackers can send malicious serialized Java objects to an exposed RMI-P4 port (typically port 50004 or 50014) and execute arbitrary code with full system privileges.
Technical Details
Impact Assessment
Critical Impact Summary
Successful exploitation grants attackers complete control over SAP NetWeaver systems with the ability to execute arbitrary OS commands, access all sensitive data, deploy ransomware, and establish persistent backdoors. The changed scope means compromise extends beyond the vulnerable component to affect connected systems and the entire SAP landscape.
Attack Methodology
Exploitation Process
Step 1: Attacker identifies exposed SAP NetWeaver systems with accessible P4/P4S ports (50004, 50014) through network scanning.
Step 2: Crafts malicious serialized Java objects using known deserialization gadget chains (e.g., Commons Collections, Spring Framework vulnerabilities).
Step 3: Sends malicious payload to the P4 port without any authentication.
Step 4: SAP NetWeaver deserializes the untrusted object, triggering the gadget chain and executing arbitrary code.
Step 5: Attacker gains command execution with SAP application server privileges, typically running as root or SYSTEM account.
Step 6: Establishes persistence, deploys additional malware, exfiltrates data, or moves laterally to other systems.
Technical Root Cause Analysis
The vulnerability stems from insufficient validation of serialized Java objects received through the RMI-P4 protocol. The affected P4-Lib component accepted and deserialized untrusted Java objects without implementing proper security controls, allowing attackers to leverage Java deserialization gadget chains to achieve code execution.
Root Cause
SAP NetWeaver's RMI-P4 implementation lacked critical security measures: no object input filtering, no class whitelisting for deserialization, and insufficient validation of incoming serialized data. This allowed attackers to inject malicious serialized objects containing gadget chains that execute arbitrary code during the deserialization process.
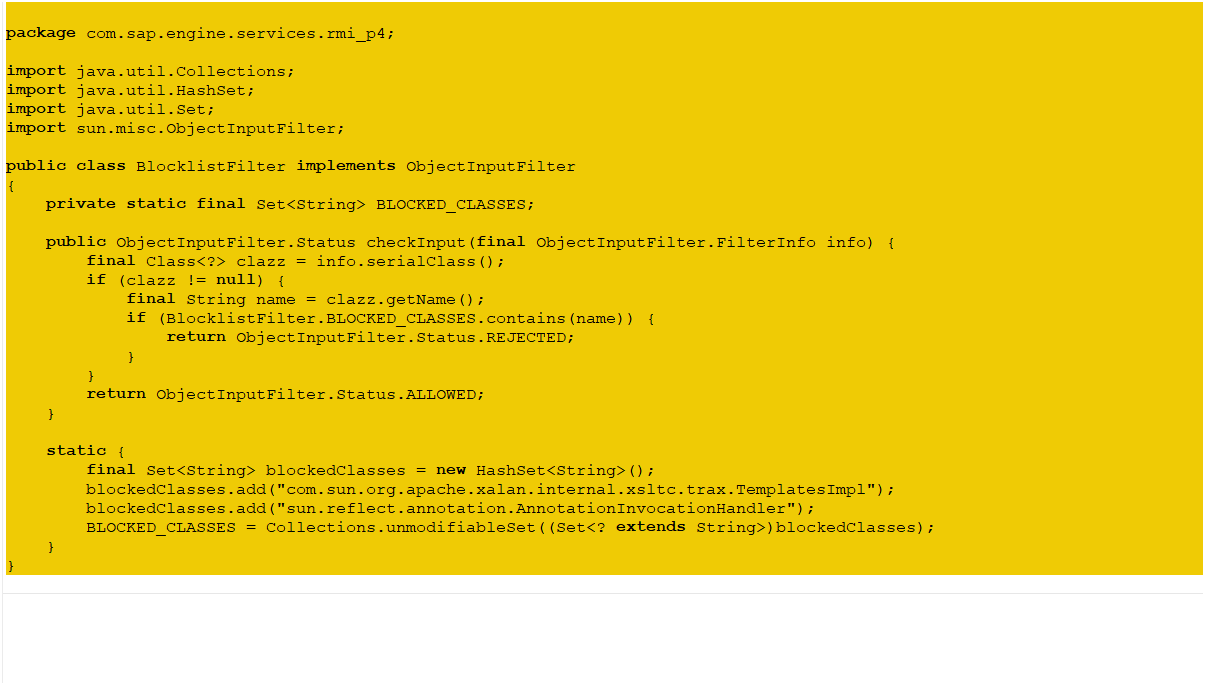
Patch Implementation: BlocklistFilter Class
The security patch introduces a BlocklistFilter class that implements ObjectInputFilter to reject dangerous classes during deserialization:
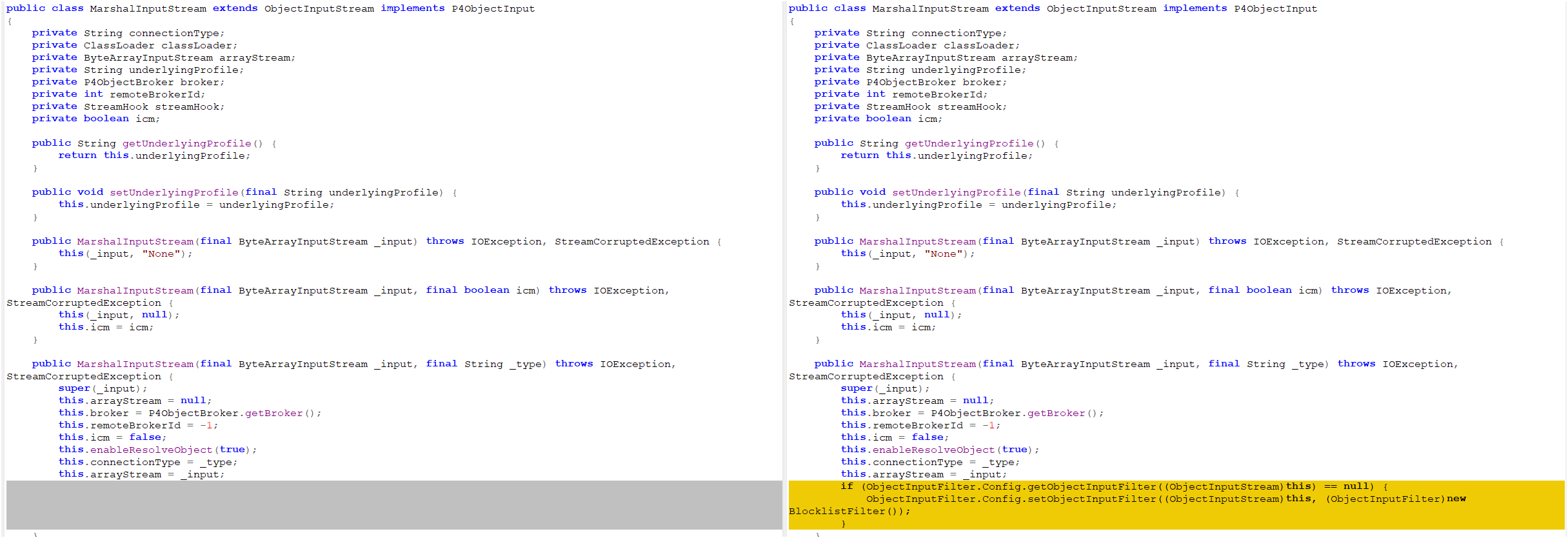
Patch Implementation: MarshalInputStream Integration
The patch modifies MarshalInputStream to integrate the BlocklistFilter, ensuring all deserialization operations validate objects against the blocklist:
Affected Software Components
Component Details
Patch Availability by Support Package
Patches are available for SP020 (Patch 000044) through SP035 (Patch 000000). Systems must be running Java 8 Update 121 or higher before applying patches. Check SAP Note 1974464 for SCA dependency analysis before updating.
Security Patch Implementation
Key Security Enhancements
ObjectInputFilter Implementation: The patch introduces Java's ObjectInputFilter mechanism to validate objects during deserialization before they are instantiated.
Class Blocklist: A comprehensive blocklist of dangerous classes is maintained, including known gadget chain classes from Apache Commons Collections, Xalan, Spring Framework, and other libraries.
Serialization Validation: All incoming serialized objects through the P4 protocol are now filtered through the BlocklistFilter before deserialization proceeds.
Defense in Depth: Additional hardening is available through SAP Note 3660659 for comprehensive protection against deserialization vulnerabilities across AS Java.
Detection and Monitoring
Network-Level Indicators
Monitor for unexpected connections to P4/P4S ports (50004, 50014) from untrusted networks or external IP addresses. Look for unusual traffic patterns including large payloads or connections from scanners and automated tools.
System-Level Indicators
Watch for Java deserialization errors in SAP logs, unexpected child processes spawned by the SAP Java process, new scheduled tasks or cron jobs created by the SAP user account, and unusual outbound network connections from SAP application servers.
SIEM Detection Rules
Alert on connections to P4/P4S ports from public IP addresses, monitor for Java ClassNotFoundException or deserialization exceptions in SAP logs, detect process creation events where parent process is SAP Java and child process is system shell (cmd.exe, bash, powershell), and flag file modifications in SAP installation directories outside maintenance windows.
Immediate Remediation Actions
1. Emergency Patching
Apply SAP Security Note 3634501 immediately. Verify Java version is 8u121 or higher (update using SAP Note 2695197 if needed). Apply additional hardening from SAP Note 3660659. Check SCA dependencies per SAP Note 1974464 before patching.
2. Network-Level Workaround (Temporary)
If immediate patching is impossible, implement network isolation: restrict P4/P4S ports (50004, 50014) to internal trusted networks only using firewall rules. Configure IP filtering at the ICM level for P4/P4S protocols. Test accessibility from untrusted networks using telnet. Review SAP MMC Access Points to verify listening interfaces.
3. System Assessment
Immediately audit all SAP NetWeaver AS Java systems for signs of compromise. Review logs for suspicious deserialization attempts or unexpected connections to P4 ports. Check for unauthorized system changes, new processes, or modified files in the SAP installation.
4. Post-Patch Validation
After applying patches, verify the BlocklistFilter is active by reviewing SAP Java logs. Test that legitimate P4 connections (SUM, Solution Manager, Integration Broker) still function correctly. Monitor for any compatibility issues with existing integrations.
Emergency Security Advisory prepared by RedRays Cybersecurity Team
Published: October 14, 2025 | Priority: MAXIMUM | Last Updated: October 14, 2025
© 2025 RedRays. CVSS 10.0 - Highest possible severity. Immediate emergency patching required.






