On December 10, 2024, SAP released Security Note 3536965, addressing multiple high-severity vulnerabilities within Adobe Document Services of SAP NetWeaver AS for JAVA. Identified under CVE-2024-47578, CVE-2024-47579, and CVE-2024-47580, these vulnerabilities pose significant risks to organizations utilizing SAP’s enterprise solutions. This blog post explores the nature of these vulnerabilities, their potential impacts, and the essential steps needed to mitigate associated risks.
Understanding the Vulnerabilities
The primary vulnerability, CVE-2024-47578, is a Server-Side Request Forgery (SSRF) flaw that allows an attacker with administrative privileges to send specially crafted requests from a vulnerable web application. This type of attack typically targets internal systems behind firewalls, which are otherwise inaccessible from external networks. Successful exploitation can enable attackers to read or modify any file on the server or even render the entire system unavailable, leading to severe disruptions in business operations.
In addition to CVE-2024-47578, two other vulnerabilities have been identified. CVE-2024-47579 allows an authenticated attacker with administrative rights to exploit an exposed web service to upload or download custom PDF font files on the system server. By manipulating the upload functionality, an attacker can copy internal files into font files and subsequently download them, gaining access to any file on the server without affecting system integrity or availability. Similarly, CVE-2024-47580 permits an authenticated attacker to create PDFs with embedded attachments, specifying internal server files as attachments. Downloading these generated PDFs enables the attacker to read any file on the server without impacting system integrity or availability.
Impact and Risks
These vulnerabilities collectively present severe threats to the security and integrity of SAP environments. Unauthorized access to sensitive files can lead to data breaches, exposing confidential business information, intellectual property, and personal data. The SSRF vulnerability, in particular, can be leveraged to pivot attacks within the internal network, potentially compromising additional systems and services. Furthermore, the ability to manipulate and access internal files without detection undermines the overall security posture, increasing the risk of regulatory non-compliance and resulting in hefty fines and reputational damage.
PoC
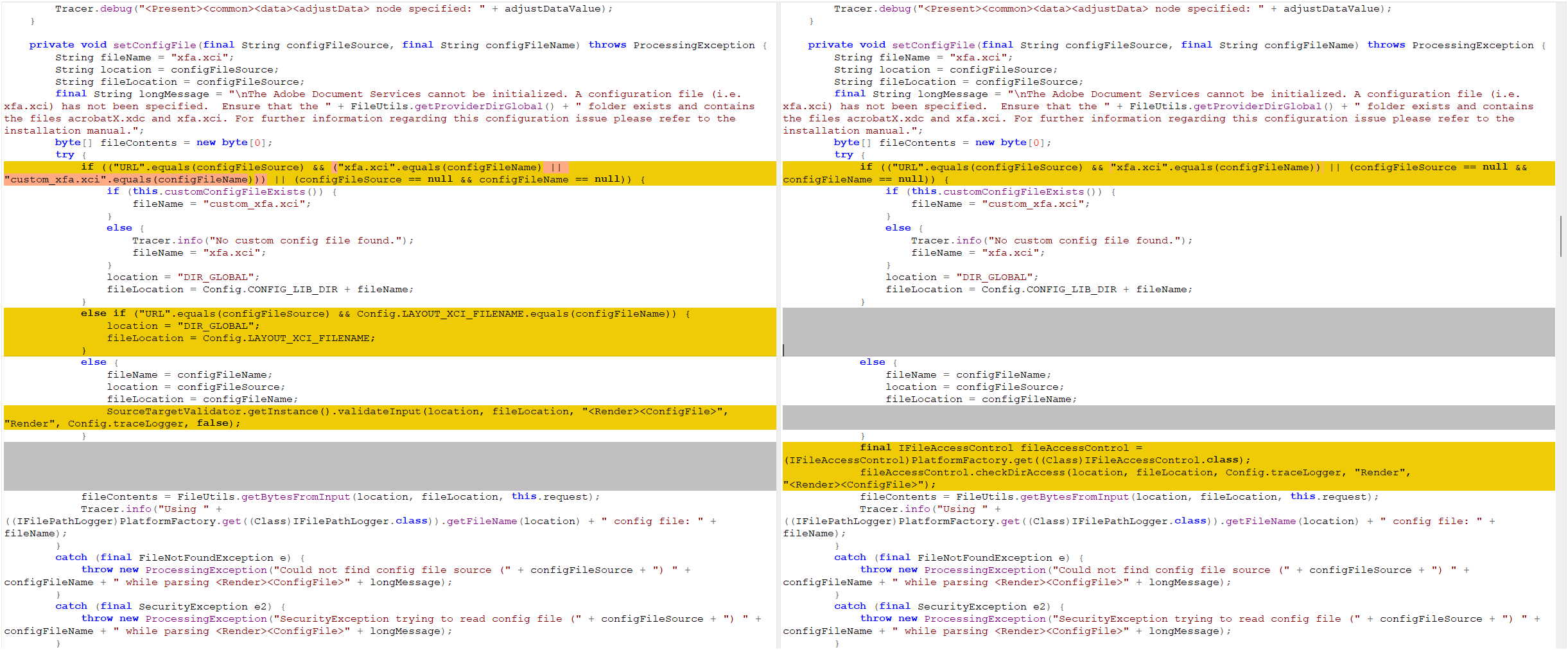
Proof of concept and vulnerability signatures are deployed in the RedRays Security Platform.
Mitigation and Remediation
Addressing these vulnerabilities requires immediate and decisive action. Organizations must apply SAP Security Note 3536965 to update Adobe Document Services to the specified patch level. This update implements necessary fixes to prevent exploitation of the identified vulnerabilities. It is crucial to deploy the patch across all affected SAP NetWeaver AS for JAVA instances without delay, especially in environments exposed to higher threat levels.
Post-update, thorough testing should be conducted to ensure that the vulnerabilities are effectively mitigated and that no functionality is adversely affected. Reviewing system and application logs for any signs of attempted exploitation prior to patch deployment is also recommended. Additionally, restricting administrative access by adhering to the principle of least privilege and implementing multi-factor authentication (MFA) for all administrative accounts can significantly reduce the risk of unauthorized exploitation.
Network segmentation is another critical measure. Isolating SAP NetWeaver AS for JAVA from other network segments minimizes the attack surface and limits potential lateral movement by attackers. Updating firewall configurations to restrict unnecessary inbound and outbound traffic to and from Adobe Document Services further enhances security.
Regular security audits, including vulnerability scanning and penetration testing, should be conducted to proactively identify and remediate security weaknesses. These practices ensure that security controls remain effective and that new vulnerabilities are promptly addressed.
Best Practices for Ongoing Security
Maintaining a robust security posture involves staying informed about the latest SAP Security Notes and updates to stay ahead of emerging threats. Automating patch management can facilitate the efficient deployment of updates across all SAP environments, reducing the window of exposure. Educating staff about security best practices and the importance of maintaining secure configurations is essential in fostering a culture of security awareness.
Developing and maintaining a comprehensive incident response plan ensures swift and effective action in the event of a security breach, minimizing potential damage and restoring normal operations promptly.
Conclusion
The discovery of multiple high-severity vulnerabilities in SAP NetWeaver AS for JAVA’s Adobe Document Services underscores the critical need for vigilant security practices within enterprise environments. The potential for data breaches, system compromises, and service disruptions necessitates immediate action to apply the recommended patches and reinforce security measures.
At RedRays, we advocate for a proactive approach to cybersecurity. Ensuring that your SAP systems are up-to-date and fortified against known vulnerabilities is paramount in safeguarding your organization’s data and maintaining operational continuity. Don’t delay—review SAP Security Note 3536965 and implement the necessary updates to protect your SAP landscape today.
For further assistance or inquiries regarding the patch deployment, please refer to SAP Note 3544926 or contact our security experts at RedRays.






