Release Date: October 8, 2024
SAP Security Note: 3503462
Component: EP-KM-ADM-CFG
Priority: Medium
CVE Identifier: CVE-2024-47594
Overview
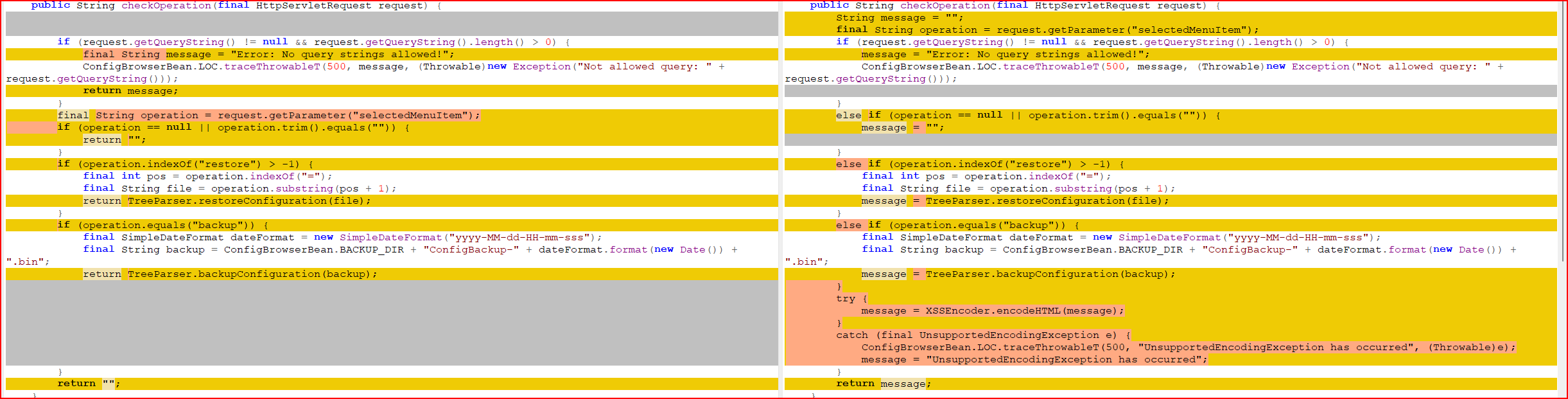
A significant security vulnerability has been identified in the SAP NetWeaver Enterprise Portal (KMC) component, designated as CVE-2024-47594. This vulnerability stems from insufficient encoding of user-controlled inputs within the KMC servlet, which can be exploited to perform Cross-Site Scripting (XSS) attacks. An attacker may craft a malicious script and deceive a registered user into clicking a specially designed link. Once the link is activated, the malicious script can execute within the user’s browser context, potentially compromising the confidentiality and integrity of their web browser session.
Vulnerability Details
The core issue arises from inadequate input validation and encoding mechanisms for user-supplied data in the KMC servlet. This oversight allows attackers to inject and execute arbitrary scripts by embedding them in links that users might inadvertently click. The exploitation of this vulnerability can lead to unauthorized access to sensitive session data and manipulation of user interactions within the portal, posing risks to both user privacy and data integrity.
Impact Assessment
This vulnerability affects all users interacting with the SAP NetWeaver Enterprise Portal (KMC) who engage with the vulnerable servlet. The primary consequence of exploiting CVE-2024-47594 is the potential hijacking of user sessions, which can result in unauthorized access to confidential information and the ability to manipulate data within the portal. While the CVSS score of 5.4 categorizes this vulnerability as medium priority, the ability to compromise user sessions underscores the importance of timely remediation.
Mitigation and Remediation
To address this vulnerability, it is imperative to apply the Support Packages and Patches referenced in SAP Security Note 3503462 without delay. These updates incorporate enhanced encoding mechanisms that effectively prevent the execution of injected scripts within the KMC servlet. Administrators should follow the standard patch installation procedures to ensure that the updates are correctly applied and that the system remains stable post-installation.
In addition to applying the necessary patches, it is advisable to review and enhance input validation processes within the Enterprise Portal. Implementing stricter encoding standards and sanitizing user inputs can further mitigate the risk of similar vulnerabilities in the future. Educating users about the dangers of clicking on suspicious links and promoting awareness of potential phishing attempts can also serve as an additional layer of defense against XSS attacks.