RedRays, a prominent company in the cybersecurity domain, recently undertook an extensive study focusing on the security of SAP systems. Our research involved a comprehensive scan of 10,000 public IP addresses associated with SAP systems. The findings from this study are both enlightening and concerning:
- Total Vulnerabilities Detected: 12,875
- Critical: 1,543
- High: 1,258
- Medium: 5,579
- Low: 4,495
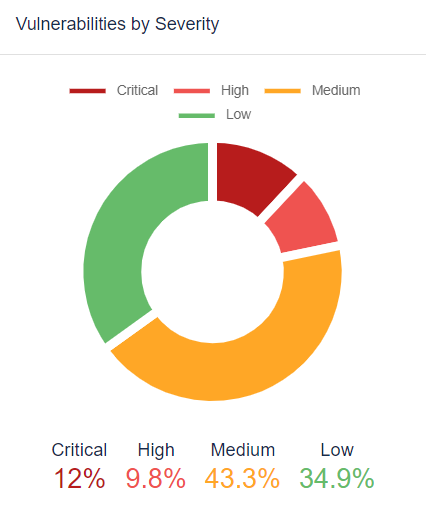
From the systems analyzed, vulnerabilities were identified in a staggering 3,094 of them. When categorized by the severity of the vulnerabilities, the distribution was as follows:
- Critical: 12%
- High: 9.8%
- Medium: 43.3%
- Low: 34.9%
Deep Dive into Critical Vulnerabilities:
- CVE-2020-6287: This vulnerability is present in SAP NetWeaver AS JAVA (LM Configuration Wizard) versions 7.30 to 7.50. It allows attackers, without any prior authentication, to execute configuration tasks, potentially leading to the creation of an administrative user. The implications of this are severe, compromising the system’s confidentiality, integrity, and availability.
- CVE-2022-22536: This vulnerability affects multiple SAP systems, including SAP NetWeaver Application Server ABAP and Java, ABAP Platform, SAP Content Server 7.53, and SAP Web Dispatcher. These systems are vulnerable to attacks related to request appending and concatenation. An unauthenticated attacker can manipulate a victim’s request, impersonating them or even “poisoning” web caches. Successful exploitation can compromise the system entirely.
- CVE-2022-41272: This vulnerability pertains to SAP NetWeaver Process Integration (PI) version 7.50. It allows an unauthenticated attacker to exploit the open naming and directory API, accessing services that can perform unauthorized operations. This can lead to unauthorized data access, data manipulation, and even degrade system performance.
- CVE-2022-41271: Similar to the above, this vulnerability is also related to SAP NetWeaver Process Integration (PI) version 7.50. It can lead to significant breaches in confidentiality, potential denial of service (DoS) attacks, and even SQL injections.
- CVE-2021-37535: Found in SAP NetWeaver Application Server Java versions 7.11 to 7.50, this vulnerability arises from the system’s failure to perform necessary authorization checks. This can lead to unauthorized data access or system functionality exploitation.
- CVE-2021-21481: This vulnerability is linked to the MigrationService in various SAP NetWeaver versions. It can allow unauthorized attackers to access configuration objects, potentially granting them administrative privileges.
- CVE-2023-23857 & CVE-2023-27497: Both these vulnerabilities highlight the lack of authentication checks in different SAP systems, allowing attackers to exploit open interfaces and perform unauthorized operations.
Furthermore, the study revealed some alarming general statistics:
- 60% of companies with critical and high vulnerabilities have an average of 2,000 employees.
- 10% of these companies are consultancy firms offering SAP system development/integration services.
- Geographically, 40% of these companies are based in the USA, while 20% are in Germany.
SAP Security with RedRays: Accessible to All
Disclaimer: Vulnerability checks were performed based on version checks without PoC execution. The IP addresses were downloaded from Shodan.






